bamboobox
前言
渗透测试真是恼人,WEB好难,被360吊打,还是回来继续学PWN,争取五一刷完Hitcon-Training,这个题不是很难,但是有两种方法可以解,自己做的时候只想到一种,这里记录一下,因为第二种简单太多了。
程序逻辑
程序主要有5个功能,Show、Add、Change、Remove和Exit,其中main退出的时候会调用开始malloc的chunk的goodbye_message函数,初步思路是覆盖这个chunk的内容为magic_addr,退出即可
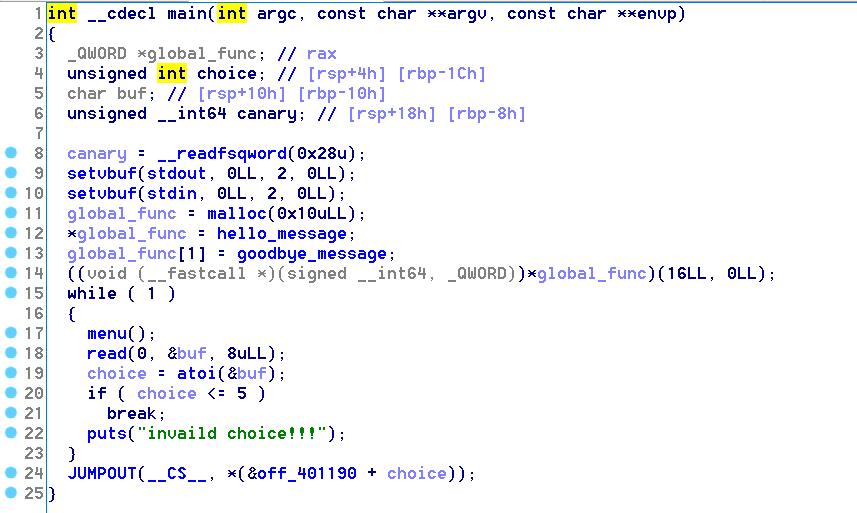
Show函数可以用来泄露地址
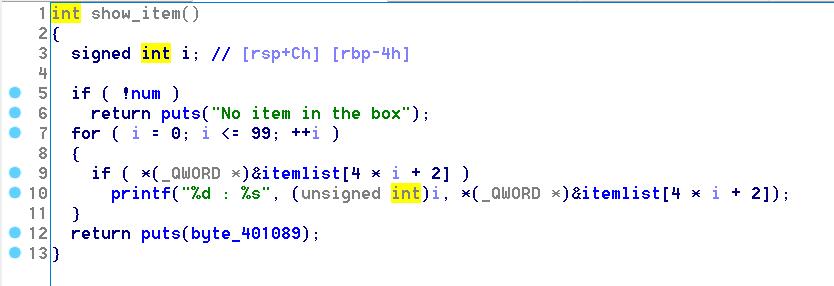
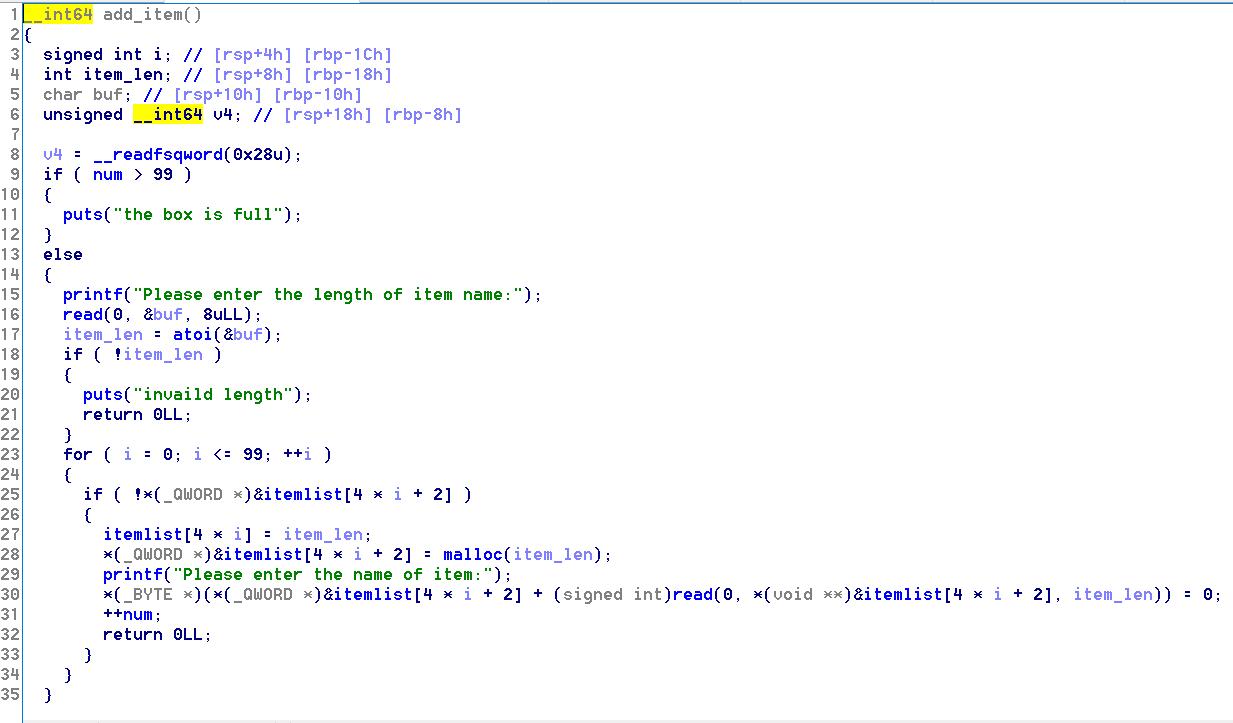
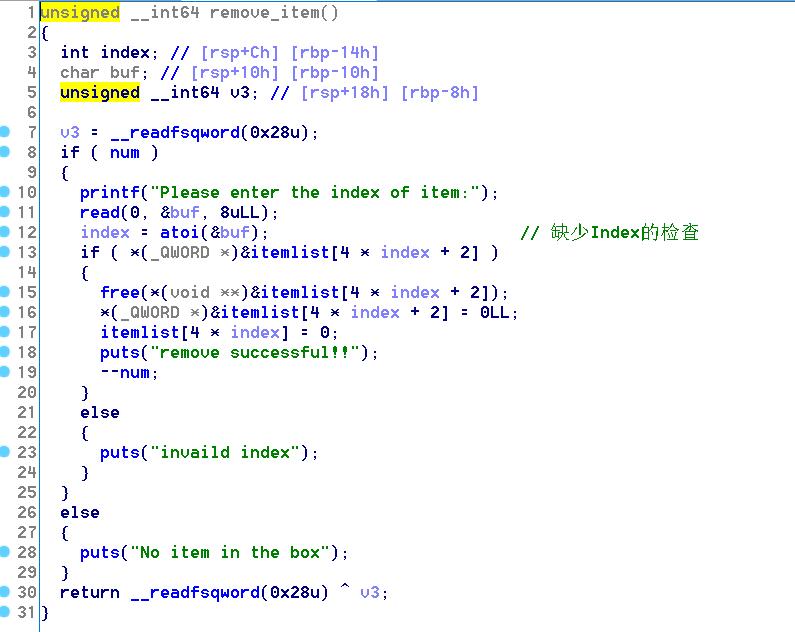
Change函数里有堆溢出
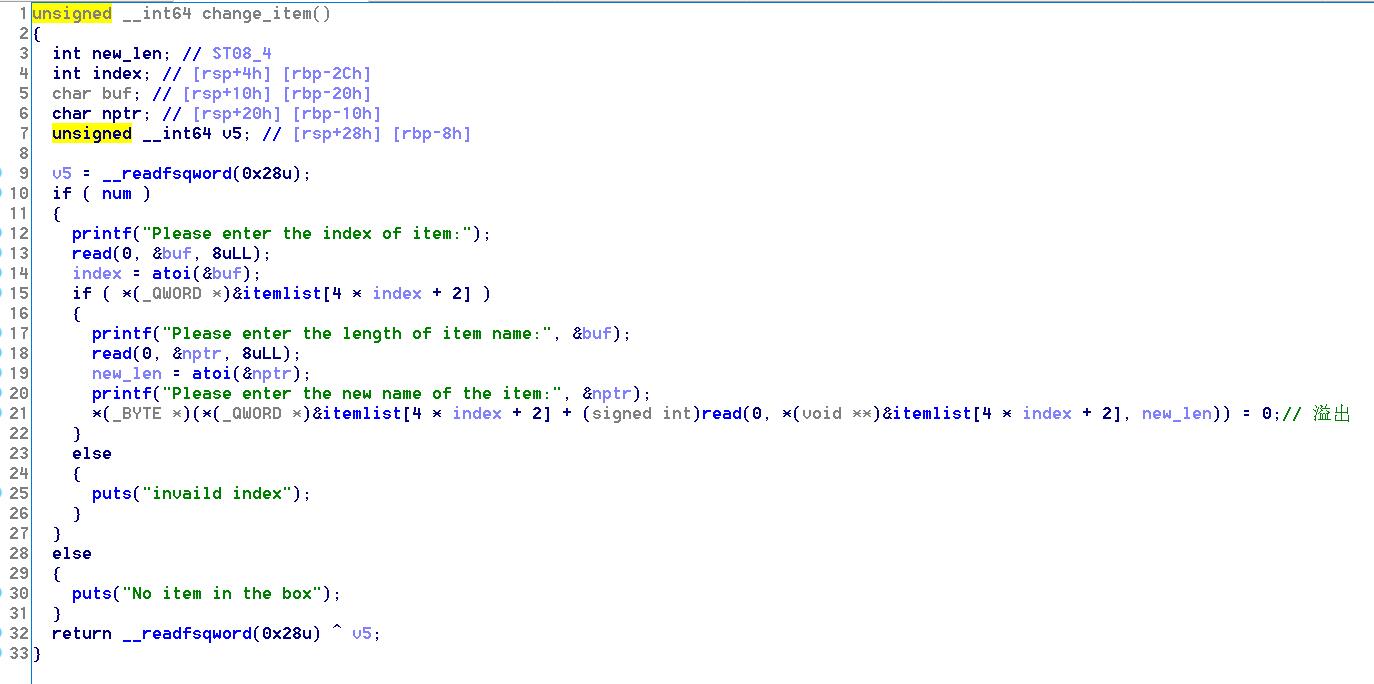
漏洞利用
method1
第一种方法是Unlink,先分配3个堆块,构造一个small chunk,chunk的结构如下:
prev_size->0
size->0x20
fd:p-0x18
bk:p-0x10
prev_size->0x20(绕过next_chunk的size检查)
nextchunk_prev_size->0x30(定位到fake chunk)
next_chunk_size->size(末尾为0,表明为空闲块)
method2
第二个方法是House of Force,在wiki里学过,思路是先分配一个chunk,溢出到top_chunk,改为
prev_size:0
size:-1
之后Malloc(-distance),distance是top_chunk到第一个chunk的距离,之后再分配chunk就会使用第一个函数所在的chunk,造成覆盖
exp.py
unlink.py
1 | #coding=utf-8 |
house-of-force.py
1 | #!/usr/bin/env python |

