tsctf2019 -> nofile
程序逻辑
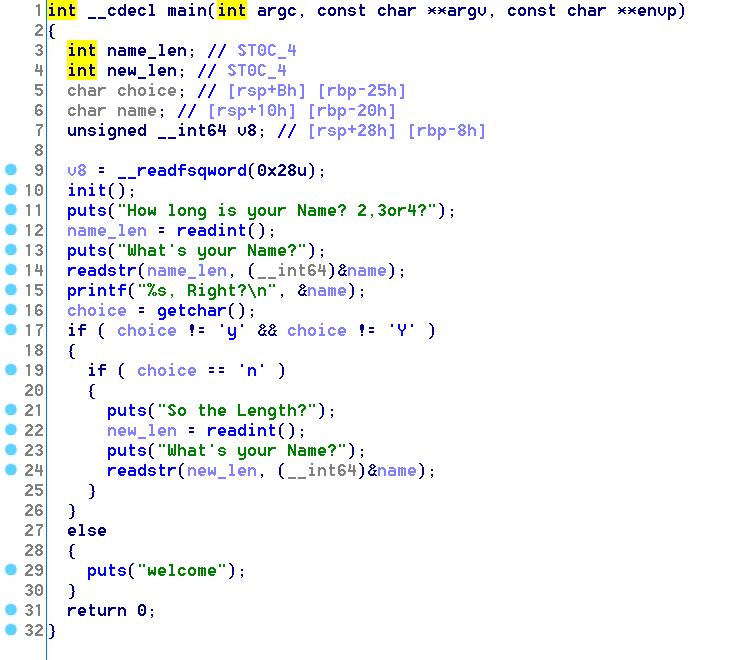
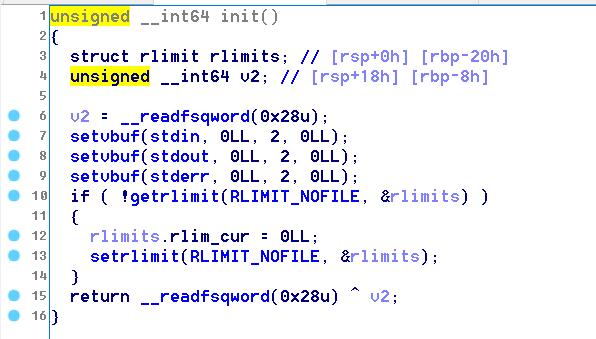
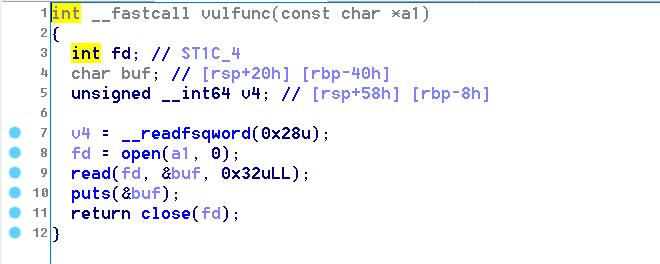
程序中main函数里首先执行Init,Init()使用setrlimit()限制了文件的描述符,导致无法打开文件分配文件描述符。程序提供了vulnfunc读取flag。
在main函数里,可以读取5个字节整数长度的数据,这里有栈溢出。之后可以重新构造数据,二次溢出
漏洞利用
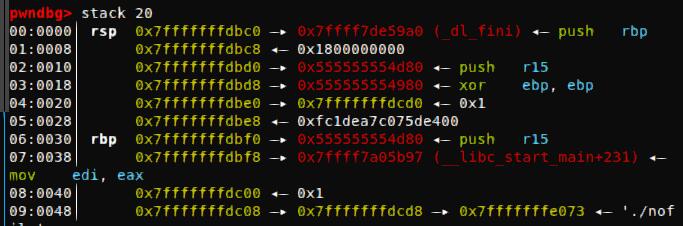
程序开了地址随机化和canary,要先泄露程序加载基地址和canary。观察一下发现rbp-8(canary)后面可泄露程序加载基址,可以构造’a’*0x18+’\n’,还原canary并得到程序加载基址。
之后拿csu的gadgets依次执行getrlimit(RLIMIT_NOFILE,bss_addr),read(0,bss_addr,100)输入构造的假的rlimit结构体,其rlimits.rlim_cur为1024。
read(0,bss_addr+0x30,100)读取”flag”,setrlimit(RLIMIT_NOFILE, bss_addr)设置fd软限制为1024
最后用pop_rdi_ret把bss+0x30作为参数传给vuln,调用这个函数即可读取flag
exp.py
1 | #coding=utf-8 |

