武汉黄鹤杯CTF
前言
错失巨款的比赛,心痛max。一共有两道pwn,pwn1的unsorted bin attack自己做的时候发现后面不太行,看ym学长的exp又学了一波正经的ub attack
note_three
漏洞利用
程序没开PIE,是partial RELOAD,程序只有New和Edit,New先让用户输入size,之后用户在0x6020c0处输入content,再使用strdup去分配堆块,注意这里是根据用户输入content长度去分配的,因此在Edit的时候会有堆溢出。
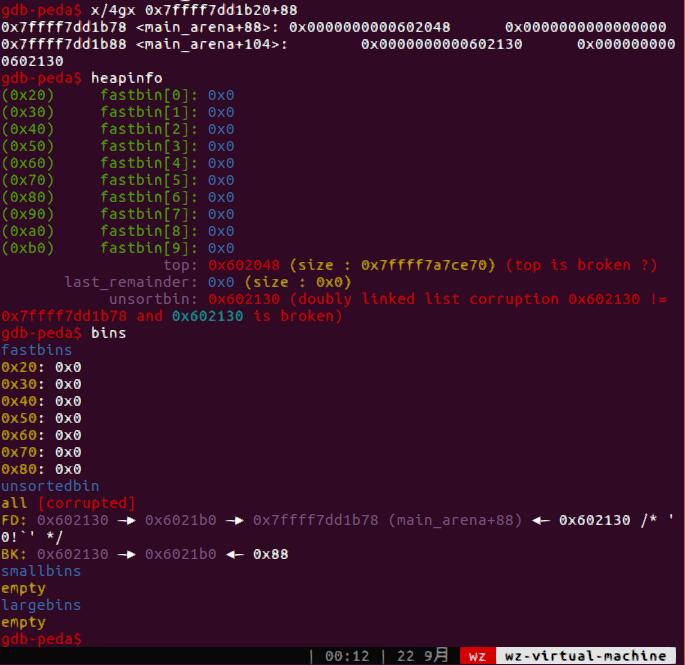
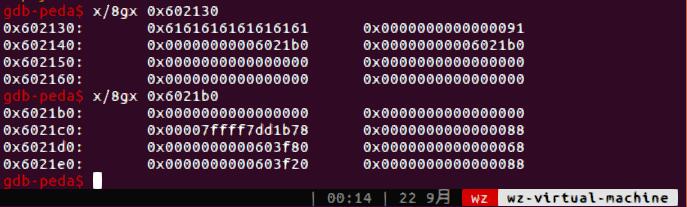
用这个堆溢出我们可以修改top_chunk的size,之后malloc大于其size的块拿到unsorted bin,之后用ub attack把heap_lis[0]改成main_arena+88(unsorted_chunk(av)),这个对应的是top_chunk,改成atoi_got-0x10,同时last_remainder改为0,为了避免Unsorted bin分配时候的检查出错,还要把其fd和bk改成一个fake_chunk的地址,这里直接在bss里构造一个fake_chunk。由于unsorted bin是按照bk寻找chunk的,因此后面从main_arena+88开始,先找到0x602130,再根据其bk0x6021b0作为寻找的最终chunk,总之这个链经过构造在分配过程中没有用非法地址,因此不会报错。
分配到aoti之后Edit改成printf,用%p泄露libc地址,再修改atoi到system拿shell。
1 | int new() |
exp.py
1 | #coding=utf-8 |
pwn2
漏洞利用
程序里有个Magic函数可以堆溢出,先House-of-orange8次拿到ub,之后tcache dup即可
exp.py
1 | #coding=utf-8 |

