magicheap
前言
两种方法,温习常规思路
程序逻辑
main函数主要有三个功能,create,edit和delete,当choice为0x1305,magic > 0x1305时我们可以看flag,magic位于bss,我们需要做一次地址任意写
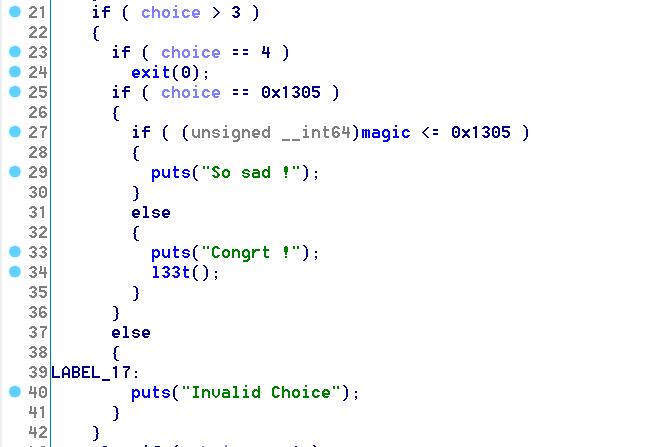
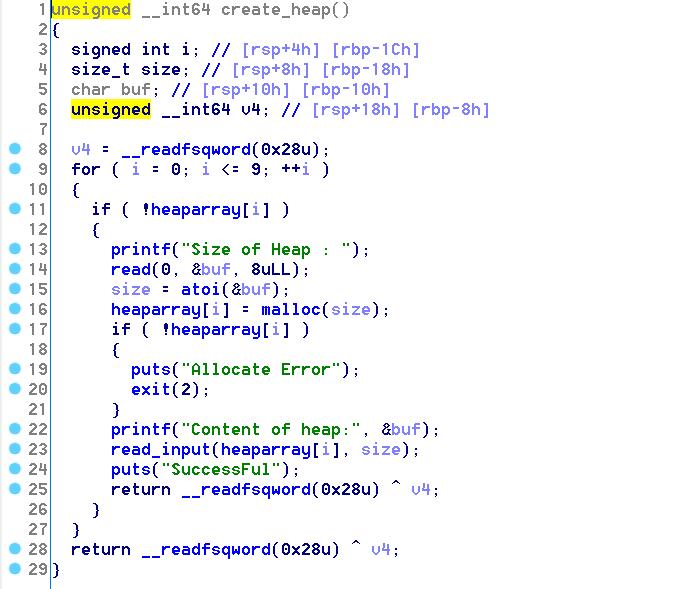
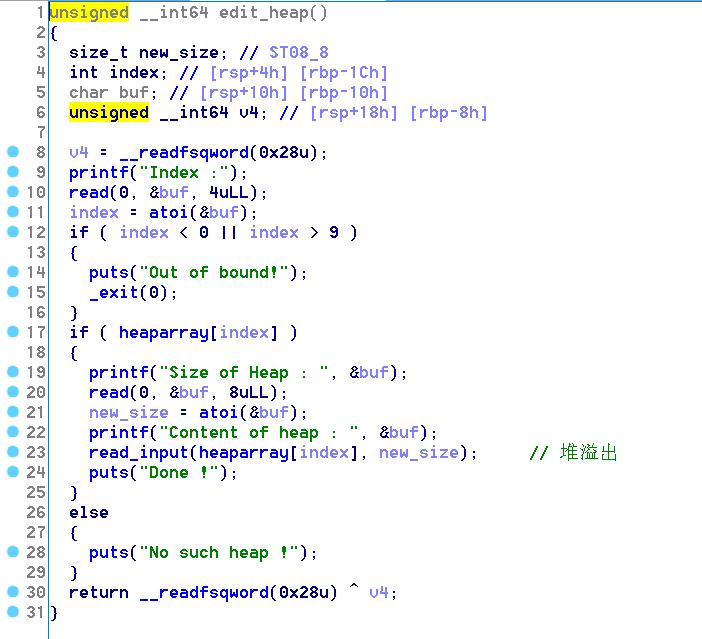
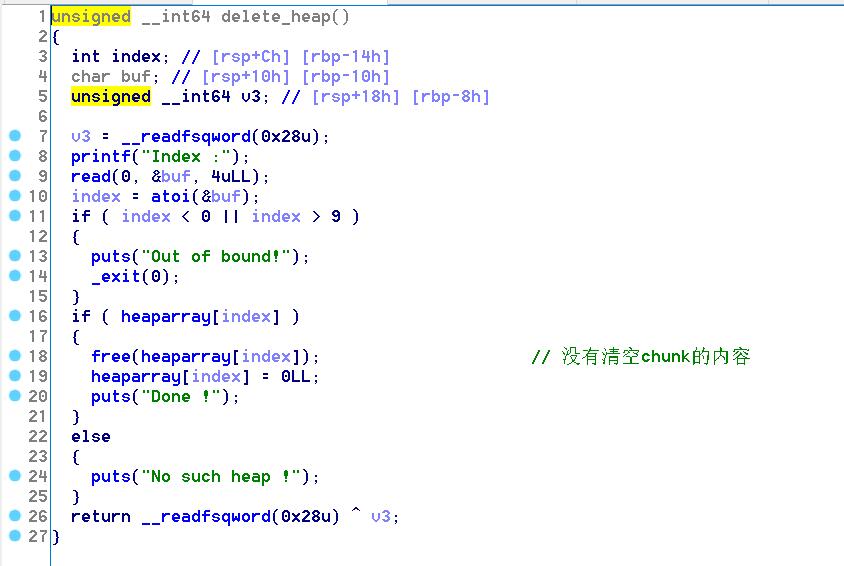
漏洞利用
第一种方法是unlink,不赘述了,注意第二个chunk分配的大小大于0x80,不能属于fastbin,伪造的chunk属于fastbin
第二种方法是unsorted bin attack,我们先建4个堆块,其中第一个和第三个是unsorted bin范围的chunk,依次free(0)、free(2),链表的结构如下:
chunk2->main_arena+88->chunk0->chunk2
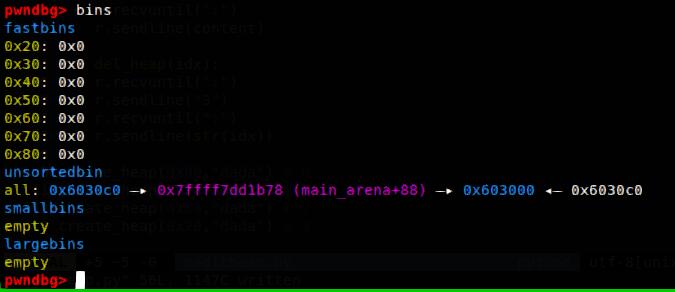
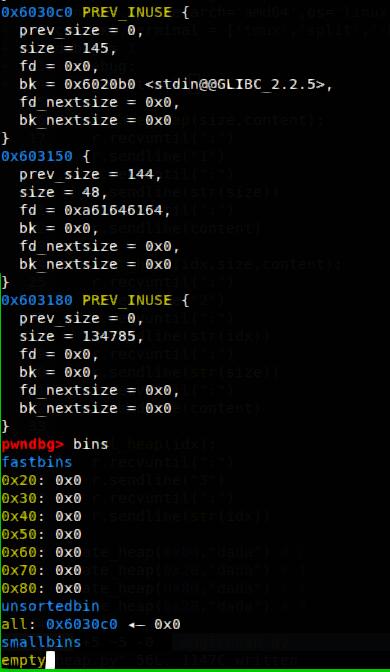
之后edit溢出覆盖chunk2的bk为magic_addr-0x10,此时bins的情况如下,最后create(0x80)使得*magic=unsorted_chunks(av)=main_arena+88,成功查看flag
unlink.py
1 | #coding=utf-8 |
unsorte-bin-attack.py
1 | #coding=utf-8 |

